# The SFTP Setup Process
SFTP (SSH File Transfer Protocol) is a way to transfer files between two remote systems securely using the SSH protocol. Within the Connector Configuration form, the following fields must be filled to setup a connection to the Trading Partner's EDL Gateway.
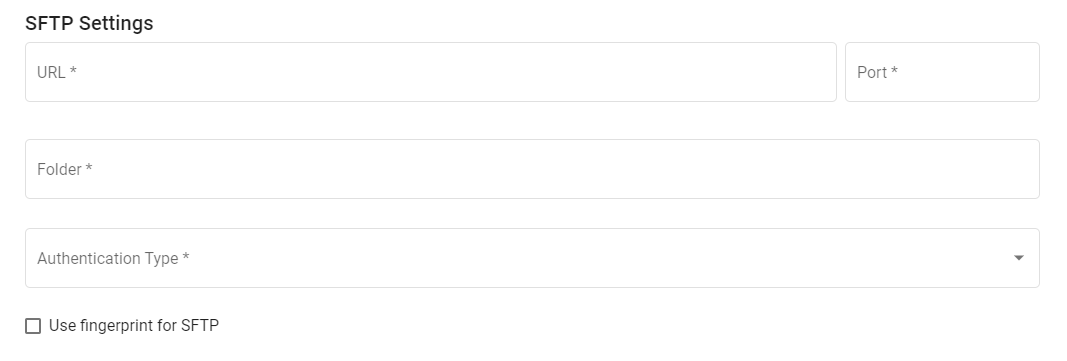
# URL
The URL refers to the location of the SFTP Server. This could be a domain URL or an IPv4 IP address.
# Port
The default and recommended port number that SFTP utilises is the SSH Port 22. However, any port number could be used by the SFTP server.
WARNING
Make sure not to use an IP Port Number that is currently in use by another IP protocol.
# Folder
The Folder field refers to the folder on the host server to poll for incoming changes.
# Authentication Types
SFTP utilises SSH for authentication methods. As such, there are three authentication types that DX2 Connectors supports: Username and Password, Private Key, and Username and Password with Private Key. There is also a supplementary authentication method of fingerprinting which is compatible with all three authentication methods.
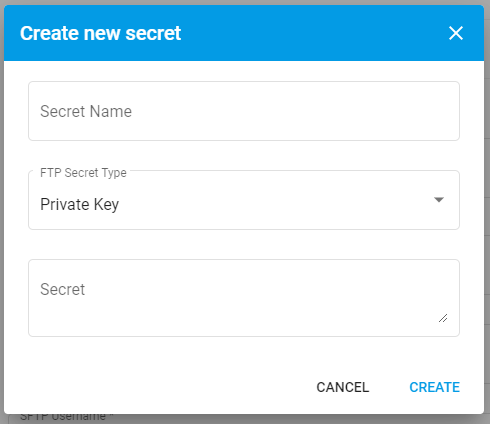
TIP
When creating a new secret, they are saved and can be reused for other related Connectors.
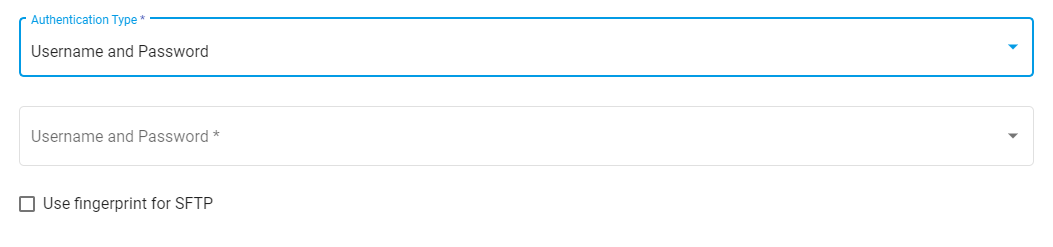
# Username and Password
One method of authentication uses the host server's Username and Password. Selecting the Username and Password option reveals another Username and Password dropdown.
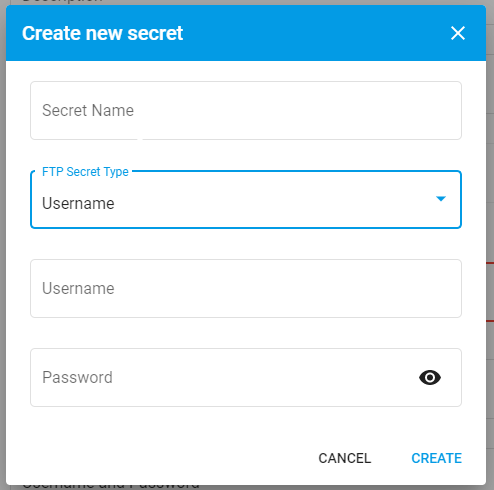
Press this new dropdown and then press Create secret .... This will then reveal a modal to generate a new secret Username and Password secret. Selecting the FTP Secret Type: Username will allow you to enter your host's Username and Password.
# Private Key
Another method of authentication is by using a SSH key pair. Selecting the Private Key option reveals a SFTP Username field and Private key secret dropdown.
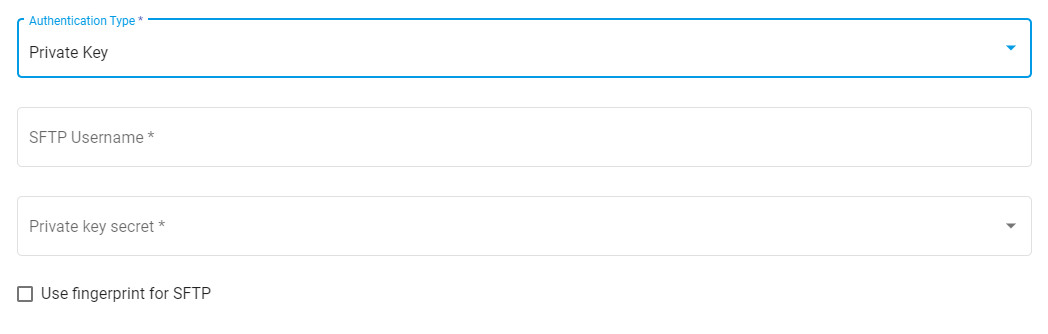
An SSH Key Pair can be generated using ssh-keygen. To learn more about SSH Key Authentication, see this article on SSH.com. Enter the Public Key given to you by the host.
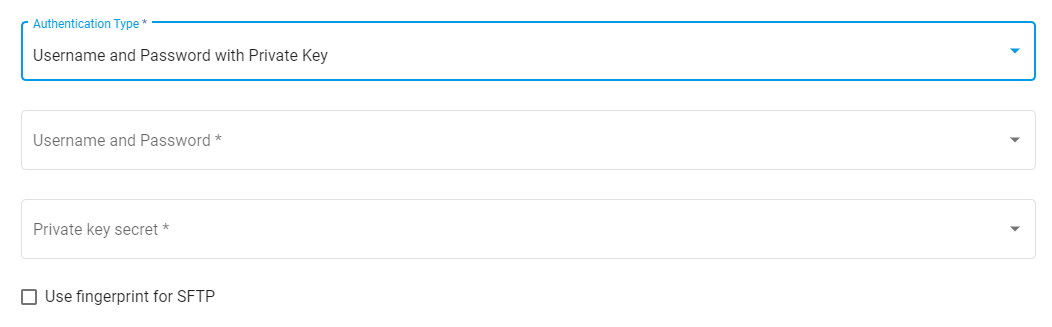
# Username and Password with Private Key
The third method of authentication is a combination of both of the previous methods. If you have created a Username and Password secret previously, select it from the dropdown. Likewise, if you have created a Private Key secret previously, then it can be reused for the same host server. Otherwise create new secrets for the two fields using the two dropdowns.
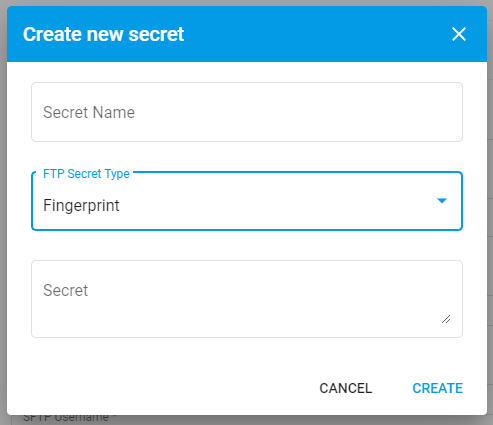
# SSH Fingerprint
To add an extra layer of security, a fingerprint secret can also be added by creating a fingerprint secret. Fingerprints are based off the host machine's public key. They are a way of ensuring that the host machine was the one which sent the message. Fingerprint secrets are created just like a Username or Private Key secret. Simply paste the host's fingerprint into the Secret field below.